Yes, it’s Orwellian, and this time around, it’s no hyperbole.
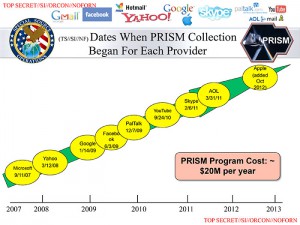
The US government apparently not only collects information (“metadata”) on all telephone calls, they also have the means collect e-mails, online chats, voice-over-IP (e.g., Skype) telephone calls, file transfers, photographs and other stored data, and who knows what else… basically, all data handled by some of the largest Internet companies, including Google, Facebook, Skype and others.
Last summer, I decided to revamp my e-mail system. The main goal was to make it compatible with mobile devices; instead of using a conventional mail client that downloads and stores messages, I set up an IMAP server.
But before I did so, I seriously considered off-loading all this stuff to Google’s Gmail or perhaps, Microsoft’s outlook.com. After all, why should I bother maintaining my own server, when these fine companies offer all the services I need for free (or for a nominal fee)?
After evaluating all options, I decided against “outsourcing” my mail system. The fact that I did not want to have my mail stored on servers that fall under the jurisdiction of the US government played a significant role in my decision. Not because I have anything to hide; it’s because I value my privacy.
Little did I know back then just how extensively the US government was already keeping services such as Google under surveillance:
From the leaked slides (marked top secret, sensitive information, originator controlled, no foreign nationals; just how much more secret can stuff get?) and the accompanying newspaper articles it is not clear if this is blanket surveillance (as in the case of telephone company metadata) or targeted surveillance. Even so, the very fact that the US government has set up this capability and recruited America’s leading Internet companies (apparently not concerned about their reputation; after all, a presentation, internal as it may be, looks so much nicer if you can splatter the logos of said companies all over your slides) is disconcerting, to say the least.
True, they are doing this supposedly to keep us safe. And I am willing to believe that. But if I preferred security over liberty, I’d have joined Hungary’s communist party in 1986 instead of emigrating and starting a new life in a foreign country. Communist countries were very safe, after all. (And incidentally, they were not nearly this intrusive. Though who knows how intrusive they’d have become if they had the technical means available.)
One thing I especially liked: the assurances that the NSA does not spy on US residents or citizens. Of course… they don’t have to. This will be done for them by their British (or Canadian?) counterparts. No agency is breaking any of the laws of its own country, yet everybody is kept under surveillance. And this is not even new: I remember reading an article in the Globe and Mail some 20 years ago, detailing this “mutually beneficial” practice. I may even have kept a copy, but if so, it is probably buried somewhere in my basement.
Meanwhile, I realize that the good people at the NSA or at Canada’s Communications Security Establishment must really hate folks like me, though, running our own secure mail servers. I wonder when I will get on some suspect list for simply refusing to use free services like Gmail that can be easily monitored by our masters and overlords.





 Yesterday, when I logged on to Google Reader, I was presented with a notice indicating that Reader will be shut down July 1st.
Yesterday, when I logged on to Google Reader, I was presented with a notice indicating that Reader will be shut down July 1st. To the esteemed dinosaurs in charge of whatever our timekeeping bureaucracies happen to be: stop this nonsense already. We no more need daylight savings time in 2013 than we need coal rationing.
To the esteemed dinosaurs in charge of whatever our timekeeping bureaucracies happen to be: stop this nonsense already. We no more need daylight savings time in 2013 than we need coal rationing. There has been a lot of discussion lately about Yahoo! CEO Marissa Mayer’s decision to ban working from home at her company.
There has been a lot of discussion lately about Yahoo! CEO Marissa Mayer’s decision to ban working from home at her company.
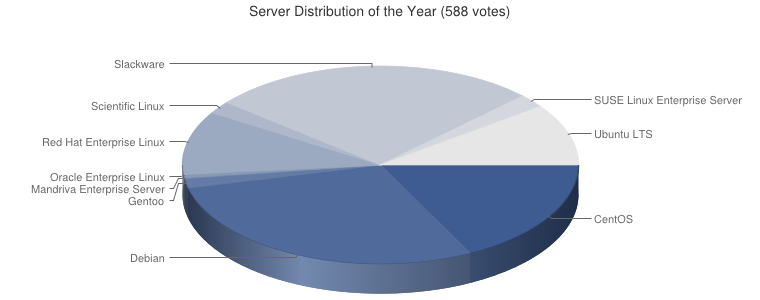
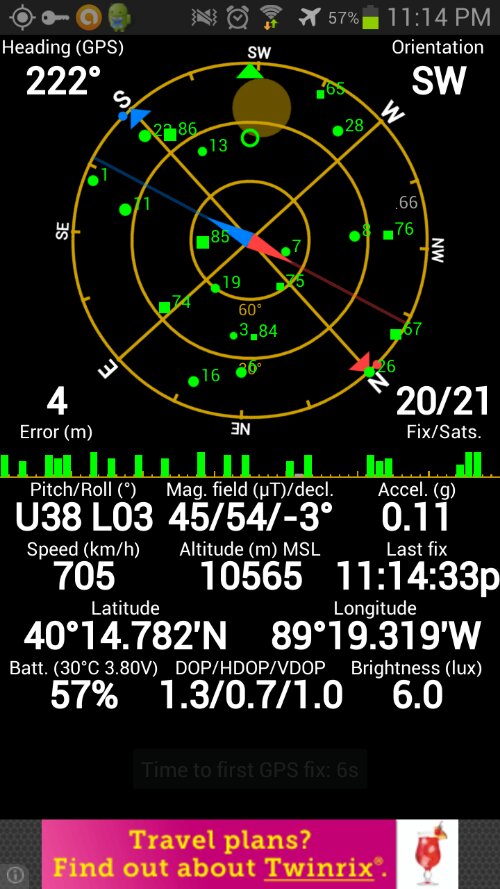

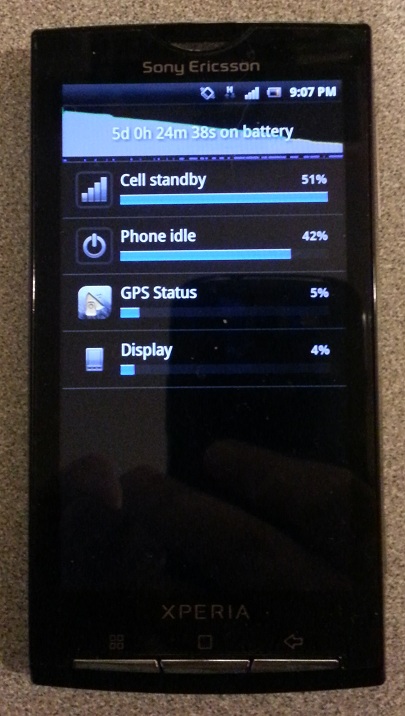
 I am supposed to be a geek but I guess I also have some chicken genes, since I never felt a particularly great urge to risk bricking my smartphone just for the sake of being able to run geeky apps on it that require root permission.
I am supposed to be a geek but I guess I also have some chicken genes, since I never felt a particularly great urge to risk bricking my smartphone just for the sake of being able to run geeky apps on it that require root permission. I use a simple WordPress plugin, called “Simple Facebook Connect”, to automatically post my blog posts to Facebook. The plugin also provides a Like button for my posts. Recently, I noticed that a number of my posts acquired a fair number of Likes from apparent strangers.
I use a simple WordPress plugin, called “Simple Facebook Connect”, to automatically post my blog posts to Facebook. The plugin also provides a Like button for my posts. Recently, I noticed that a number of my posts acquired a fair number of Likes from apparent strangers.