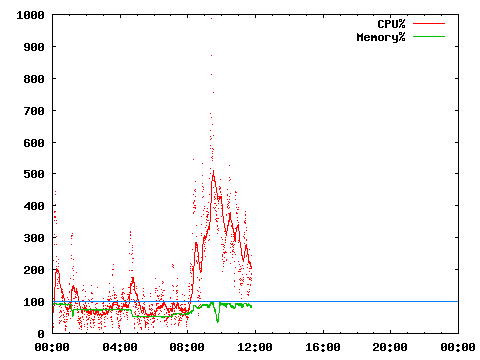
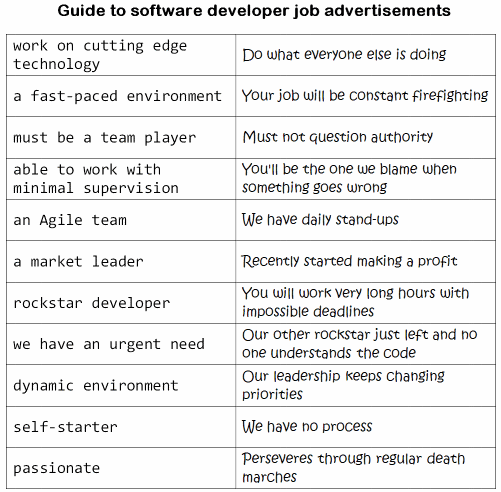
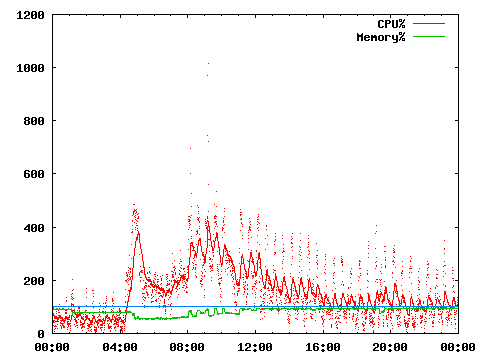
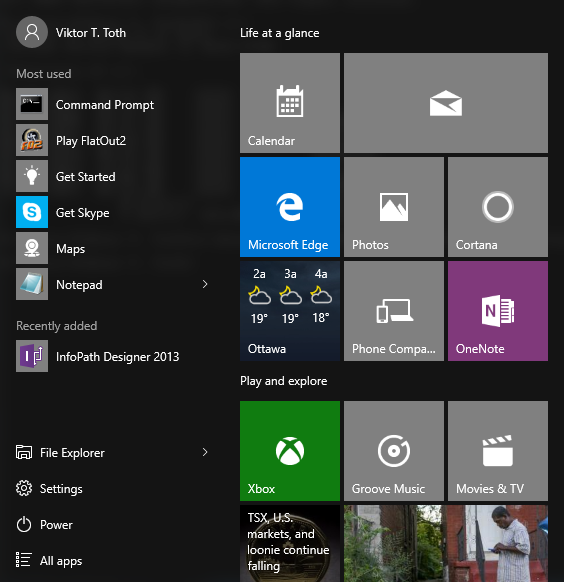
I have never been to the ghost city of Pripyat, evacuated in the wake of the Chernobyl nuclear disaster.
However, in recent days, I spent some of my free time fighting mutants, mercenaries, bandits and fanatics in and around a virtual version of Pripyat, in the game S.T.A.L.K.E.R. – Call of Pripyat.
This game is the third installment in the S.T.A.L.K.E.R. series, made by Ukrainian game developer GSC Game World.
And it is a damn good game (available without crippling DRM, courtesy of GOG.com; which is the only reason I purchased the game, as I do not buy DRM-protected crippleware.) The other two games are pretty darn good, too.
The games combine an iconic science fiction novella by Arkady and Boris Strugatsky with the realities of the Chernobyl Exclusion Zone (officially the Chernobyl Nuclear Power Plant Zone of Alienation.)
The novella, Roadside Picnic, is inspired by a vision of some careless visitors near a forest, who, after a brief stop, leave behind everything from trash to discarded spark plugs, perhaps a pocket knife or a forgotten transistor radio, or maybe even a pool of used motor oil. What do these strange, sometimes dangerous artifacts and anomalies mean to the forest’s animals? Now imagine a visit to the Earth by some equally careless members of an extraterrestrial supercivilization, with us playing the role of the forest’s fauna. What would we make of the often deadly, totally incomprehensible anomalies and artifacts? As such, the Visitation Zones become places of interest to all, including “stalkers”, freelancers who defy government restrictions and risk life and limb as they enter the Zone illegally to retrieve precious artifacts and substances from the Zone.
The novella was written 15 years before the Chernobyl disaster and its setting is a fictitious town in Canada. Nonetheless, the parallels between the novella’s fiction and Chernobyl’s reality are eerily striking: abandoned buildings, abandoned military equipment, locations with a dangerous buildup of radiation, not to mention what remained a still operating nuclear power plant for many years at the very center of the Exclusion Zone.
This, then, is the setting of the S.T.A.L.K.E.R. series of games: The Zone, its abandoned industrial facilities, farms, vehicles and equipment, the town of Pripyat, even the nuclear plant itself, complete with its sarcophagus. In the fictitious storyline of the games, the 1986 disaster was followed by another man-made disaster some 20 years later, as the Zone, now largely uninhabited, was used as a place to conduct secret, often unsanctioned research.
Near the end of the third game, the player is presented with a choice of being part of an evacuation (which ends the game) or staying in Pripyat. I opted to stay. (OK, I had a saved game, so of course I could explore both scenarios.) After the helicopters left, I still had to dispatch a few enemies… but after that, there I was, standing in the middle of a square in Pripyat in the dead of night, with no friends, not even enemies, just silence occasionally broken by the howl of mutants in the distance. My safe house was gone, all I had was the equipment I carried… and I was alone.

I was honestly surprised by the intensity of this feeling of loneliness coming from a computer game.
Anyhow, I survived, morning came, and I was able to explore parts of Pripyat that I did not visit during the more intense game playing earlier. And thus, I happened upon a famous Pripyat landmark, the town’s never used Ferris wheel:

The Ferris wheel, along with the rest of Pripyat’s brand new amusement park, was set to open on May 1, 1986; unfortunately, the power plant disaster on April 26 scuttled those plans.
Sadly, I was unable to explore the Ferris wheel up close; it is located outside the region of Pripyat that is accessible to the player. But the area that can be explored is huge and terrifyingly gloomy, looking a little bit like pictures from North Korea:

As to the abandoned Soviet-era facilities, here is a splendid example:

Hey, when I took that screen shot, the Sun was almost shining!
The Sun was not shining, though, when I visited the Chernobyl nuclear plant in one of the earlier installments of the game:

But what a place it was. Mostly quiet deadly, even with the best equipment my game persona could muster.
Oh well, it was fun to play these games. Time to get back to work, though.







 It was 25 years ago today that a Finnish chap by the name of Linus Torvalds made an announcement about a new operating system that he developed in the preceding few months. Nothing big and professional, he assured us, just a hobby project basically… but here it was, and he already got a command shell and the GNU C compiler working.
It was 25 years ago today that a Finnish chap by the name of Linus Torvalds made an announcement about a new operating system that he developed in the preceding few months. Nothing big and professional, he assured us, just a hobby project basically… but here it was, and he already got a command shell and the GNU C compiler working.