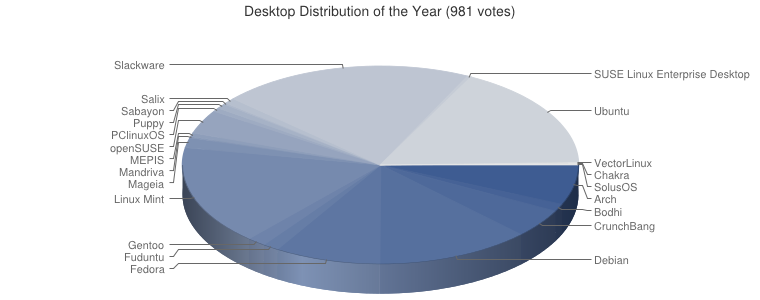
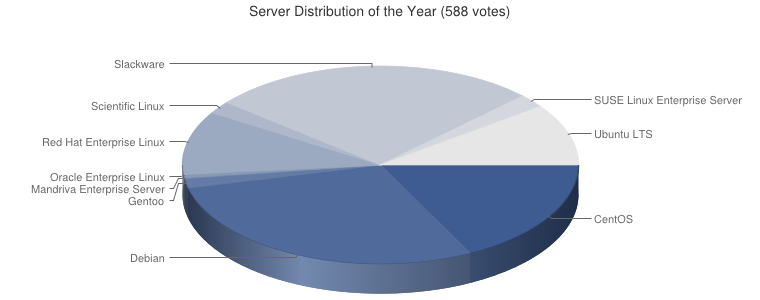
Visitors to my blog or Web sites may have noticed that in the past week, my Web pages loaded more slowly than usual, and may even have been unavailable at times.
Visitors to my blog or Web sites may have noticed that in the past week, my Web pages loaded more slowly than usual, and may even have been unavailable at times.
The reason: shortly before noon, July 30, I lost my primary Internet connection.
This connection was via a legacy DSL service (bridged DSL) to a company that used to be UUNet Canada, was purchased by MCI, and eventually, by Verizon, and now does business under the Verizon Canada name.
Yes, the same Verizon that is about to enter the Canadian wireless market, much to the concern of Canada’s “big three”, Bell, Rogers and Telus.
I noticed the service interruption essentially immediately, and reported it to Verizon. First, they suggested that it was a telco problem; indeed, Bell Canada even wanted to send out a technician, but fortunately, I was able to talk them out of this. (The DSL modem was connecting just fine.)
The service was not restored the next day, nor on August 1. But on August 1, I had a long discussion with a Verizon technician. The first thing I learned is that the technician resides in the Philippines. Back in the old days, when I had a technical issue with UUNet Canada, I usually ended up talking to an engineer in their Toronto network operations center, and my issue was resolved in minutes. Don’t get me wrong, the Philippines technician spoke accent-free English and had a basic level of understanding of the technology; but no real competence and, obviously, no decision-making authority.
What the technician did explain, however, is that Verizon made a colossal screw-up: they decommissioned some of their point-of-presence equipment here in Ottawa without first moving all customers who were still using said equipment. The technician told me that they were scrambling to find a solution, and I’ll be back up and running within a few days.
Well… that was August 1. A long weekend then came and went, but still, no Internet service. So on Tuesday, August 5, I called Verizon Canada. Their main 800 number was answered by a pleasant sounding young lady (an intern, I later learned) but on my first two calls, she managed to connect me to two different voice mailboxes, whereas on the third try, I got disconnected. On the fourth try, she made a real effort to reach someone within the company. She was ready to give up (providing me with an e-mail address instead) but when I told her that I’d rather wait on hold a little longer, she finally managed to get me connected to a senior manager.
This gentleman was friendly and competent enough, and certainly understood and appreciated the severity of my situation. I explained to him that I was already taking steps to switch to Bell Canada as my primary Internet provider. He promised to look into my situation and find a solution. He asked for a day. I asked him to call me this morning, because I wanted to make a decision today, one way or another.
He called indeed at the promised time, but all he could tell me was that he was still waiting for some technical folks to come out of a meeting. Okay, we agreed that he’d call again before 2 PM. He sent an e-mail at 2:09 PM, saying that it would take just a tad longer.
At 3:45 PM, I e-mailed and then called him. No answer. So a few minutes later, it was the end of the line for me: I called and e-mailed again, this time instructing Verizon to terminate my service. I then contacted Bell and asked them to initiate setting up my new account.
Now let’s be clear for a moment: I am not talking about some cheap $20/month wireless contract. I was paying★ a premium, to the tune of several hundred dollars, to Verizon for this service. And I’ve been their customer (with a a short interruption) since way back in 1994. If my experience is indicative of the kind of service Verizon provides, all I can say to people cheering the prospects of Verizon’s entry into the Canadian wireless market is to be careful what they wish for.
It will be a few days before my new service with Bell is up and running. I am sure there will be headaches, but I am hopeful that it won’t be too much of a hassle. Meanwhile, I am relying on a backup service that I set up two years ago with Rogers, when my Verizon service was down for a few days (that time, it was actually Bell’s fault, or so I was told.) This service is a little slower, but at least it works (for now).
★I said “I was paying a premium”, but in the last few months, I really wasn’t. Not my fault… I really tried giving them my money. Earlier this year, Verizon moved their Canadian business customers to their pre-existing Enterprise system that combines billing, online payments, service calls, etc. I dutifully set up my account as instructed and made many attempts to pay. The system accepted my credit card, informed me that my payment was processed, but charges never actually appeared on my credit card account. Last month, I contacted Verizon and after some lengthy phone calls with their billing department, also located in the Philippines, they finally told me that the problem has been found and fixed. Well… no charges appeared on my credit card account yet. Funny thing is, when I check with Verizon, my account there shows no arrears. What can I say? If they don’t want my money… I just hope that if they do come to their senses and collect the outstanding invoice amounts, they don’t actually try to charge me for the month of August… the service, after all, went away on July 30 and it was never restored.
 Electronic mailing lists are a somewhat old-fashioned way to let a group of people stay in touch and communicate about a topic of interest.
Electronic mailing lists are a somewhat old-fashioned way to let a group of people stay in touch and communicate about a topic of interest.



 Visitors to my blog or Web sites may have noticed that in the past week, my Web pages loaded more slowly than usual, and may even have been unavailable at times.
Visitors to my blog or Web sites may have noticed that in the past week, my Web pages loaded more slowly than usual, and may even have been unavailable at times.

 Today I realized that in the past month, my blog has once again become what blogs were meant to be originally: a write-only medium that nobody reads.
Today I realized that in the past month, my blog has once again become what blogs were meant to be originally: a write-only medium that nobody reads.




 Yesterday, when I logged on to Google Reader, I was presented with a notice indicating that Reader will be shut down July 1st.
Yesterday, when I logged on to Google Reader, I was presented with a notice indicating that Reader will be shut down July 1st. To the esteemed dinosaurs in charge of whatever our timekeeping bureaucracies happen to be: stop this nonsense already. We no more need daylight savings time in 2013 than we need coal rationing.
To the esteemed dinosaurs in charge of whatever our timekeeping bureaucracies happen to be: stop this nonsense already. We no more need daylight savings time in 2013 than we need coal rationing. There has been a lot of discussion lately about Yahoo! CEO Marissa Mayer’s decision to ban working from home at her company.
There has been a lot of discussion lately about Yahoo! CEO Marissa Mayer’s decision to ban working from home at her company.