Whenever I travel, I think a lot about Internet security. For purely selfish reasons: I do not wish to become a victim of cybercrime or unnecessarily expose my own systems to attacks.
The easiest way to achieve end-to-end encryption is through a virtual private network (VPN). Whenever possible, I connect to my own router’s VPN service here in Ottawa before doing anything else on the Interwebs. The connection from my router to the final destination is still subject to intercept, but at least my connection from whatever foreign country I am in to my own network is secure.
A VPN has numerous other advantages, not the least of which is the fact that to the outside world, I appear to have an Ottawa-based IP address; this allows me, for instance, to use my Netflix subscription even in countries where Netflix is not normally available.
The downside of the VPN is that I am limited by the outgoing bandwidth of my own connections. But in practice, this does not appear to be a serious limitation. (I was able to watch Breaking Bad episodes just fine while in Abu Dhabi.)
Unfortunately, a VPN is not always possible, as some providers, for reasons known only to them, block VPNs. (I can think of a few workarounds, but I have not yet implemented any of them.) Even in this case, I remain at least partially protected. I have set up my mail server such that both incoming (IMAP) and outgoing (SMTP) connections are fully encrypted. This way, not only are my messages secure, but (and this was my main concern) I also avoid leaking sensitive password information to an eavesdropper.
When it comes to Web sites, I use secure (HTTPS) connections whenever possible, even for “mundane” stuff like innocent Google searches. I also use SSH if necessary, to connect to my servers. These days, SSH is an absolute must; the use of Telnet is just an invitation for disaster.
But of course the biggest security risk while one is on the road is the use of a public Wi-Fi network anywhere. Connecting to an HTTP (not HTTPS) server through a public Wi-Fi network and logging in with your password may not be the exact equivalent of telegraphing your password to the whole wide world, but it comes pretty darn close. Tools that can be used to scan for Wi-Fi networks and analyze the data are readily available not just for laptops but even for smartphones.
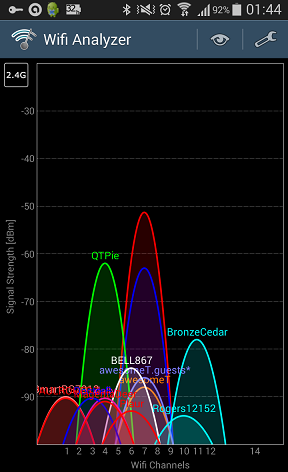
Once an open Wi-Fi network is identified, “sniffing” all packets becomes a trivial exercise, with downloadable tools that are readily available. Which is why it is incomprehensible to me why, in this day and age, most providers (e.g., hotels, airports) that actually do require users to log in use an unsecure network and just intercept the user’s first Web query to present a login page instead, when the technology to provide a properly secured Wi-Fi network has long been available.
In the future, no doubt I’ll have to take even stronger measures to maintain data security. For instance, the simple PPTP VPN technology in my router has known vulnerabilities. Today, it may take several hours on a dedicated high-end workstation to crack its encryption keys; the same task may be accomplished in minutes or less on tomorrow’s smartphones.
So there really are two lessons here: First, any security is bettern than no security, as it makes it that much harder for an attacker to do harm, and most attackers will just move on to find lower hanging fruit. Second, no measure should give you a false sense of security: by implementing reasonable security measures, you are raising the bar higher, but it will never defeat a determined attacker.

 It was 25 years ago today that a Finnish chap by the name of Linus Torvalds made an announcement about a new operating system that he developed in the preceding few months. Nothing big and professional, he assured us, just a hobby project basically… but here it was, and he already got a command shell and the GNU C compiler working.
It was 25 years ago today that a Finnish chap by the name of Linus Torvalds made an announcement about a new operating system that he developed in the preceding few months. Nothing big and professional, he assured us, just a hobby project basically… but here it was, and he already got a command shell and the GNU C compiler working.







 Notice to Web advertisers: If you stick a video on a Web page that starts with blaring noise in the middle of the night, the only thing you accomplish is that I close the bleeping page in a mad panic, and I make sure never to visit it again.
Notice to Web advertisers: If you stick a video on a Web page that starts with blaring noise in the middle of the night, the only thing you accomplish is that I close the bleeping page in a mad panic, and I make sure never to visit it again.