So everyone is talking about the major IT outage today (which actually turned out to be two unrelated outages, the second due to a since-remedied issue with Microsoft Azure platform), namely the fact that millions of physical computers and virtual machines around the world are crashing due to a driver failure in what is known as CrowdStrike Falcon.
I admit I have not heard of CrowdStrike Falcon before. I had to look it up. So I went to the most authoritative source: the company’s Web site.
“Cybersecurity’s AI-native platform for the XDR era,” it tells me, and “We stop breaches”. XDR is supposedly “extended detection and response”. Wikipedia tells me that “the system works by collecting and correlating data across various network points such as servers, email, cloud workloads, and endpoints”. Microsoft tells me that XDR “is a holistic security solution that utilizes automation and AI to reduce response time across multiple workloads”.
Going back to CrowdStrike, I learn that it yields $6 of return for every $1 invested. (How?) That it identifies 96% more potential threats. (More than what? More dentists use…) It tells me that it is leads to 2x as effective security teams with 66% faster investigations… compared to what?
Okay, scrolling down… it’s “cloud-native”, “single-platform” and an “open and extensible ecosystem”. It is “data-centric” and “AI-native” with “workflow automation”.
So far there is one thing I have not yet learned: What the bleepety-bleep does it do?
Of course I can guess. I know what security solutions are supposed to do, and I have no doubt that CrowdStrike delivers… more or less, probably not any better than its major competitors. But they certainly have good marketing, with all the right buzzwords!
Unfortunately, behind these buzzwords there is a flawed mentality. The implication that all it takes is a fancy software solution to protect your enterprise. Never mind that a good chunk of the threats (I was going to say, “vast majority”, but I have no data to back that up) are not in the form of malware. If I communicate with a senior manager at a bank and convince them to initiate an important transfer that later turns out to be fraudulent, no cybersecurity is going to prevent that.
And as today’s example shows, protection from malware and other technological threats is just one element of a successful cybersecurity policy. A comprehensive policy must be based not just on prevention but also the recognition that sometimes, despite your best efforts, excrement can hit the ventilator. How do you detect it? What do you do?
That leaves us to these main points that must be on everyone’s cybersecurity checklist, whether you are a small company or a major international enterprise. Here, in no particular order, and I am sure I left some things out:
- Threat prevention (technological prevention, such as antivirus software, network firewalls, real-time monitoring)
- Data collection (comprehensive logs that may be used for threat detection, forensic analysis, mitigation)
- Compartmentalization (user privileges, user access management, network architectures)
- User relationships (user education, use management — treating users as partners not as threats)
- Backup and recovery procedures and policies, tested (!) and validated
- Intrusion detection
- Intrusion response (emergency operations, fallback operations including manual operations if needed, notification policy)
- Mitigation, self and third-party impact
- Recovery
- Forensic analysis and prevention
- Auditing and risk analysis (including third party dependence)
I mean, come on, CrowdStrike’s graphic is eye-catching but I swear I drew much more informative diagrams well over a decade ago when educating customers about the need for comprehensive security. Like these, for instance.
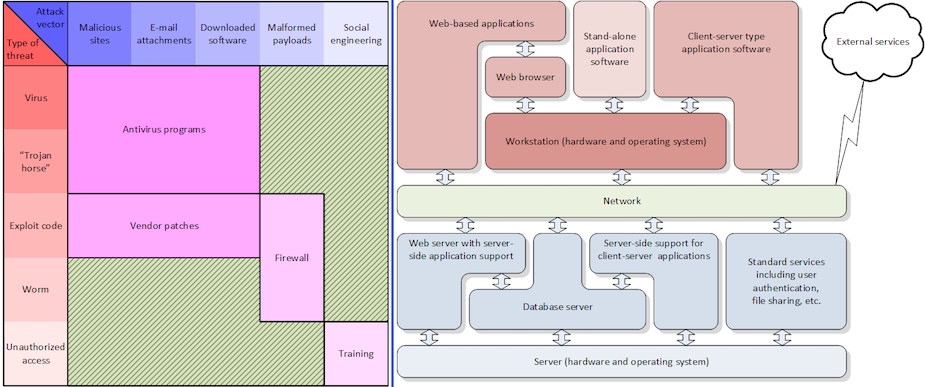
Sure, comprehensive cybersecurity technology can help with some of these points. But not all. For instance, no cybersecurity solution will help you if broad dependence on a third-party component in your enterprise suddenly causes a widespread outage. That dependence can be anywhere, could be a simple messaging app or a complex cybersecurity suite. If it causes systems to crash, and you have no proven, tested policies and practices to detect, mitigate, and recover from an event like that, you’re in deep doo-doo.
Oh wait. That’s exactly what happened to far too many companies today.